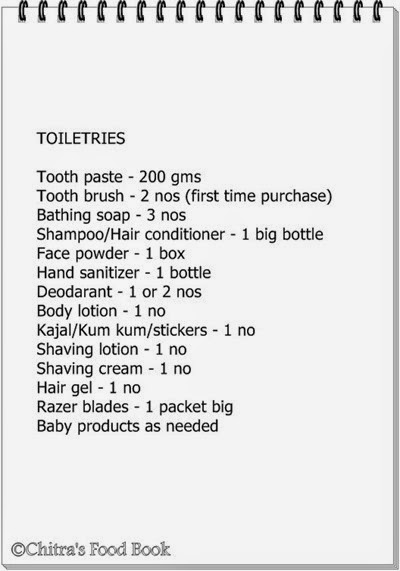
Maligai Saman List In Tamil Excel
List of Indian Spices in English, Tamil, Telugu, Kannada and Hindi Glossary of Spices in Indian Languages and English: pin. Grocery List Maligai Saman List Grocery Shopping List 11:52: pin. GST- Explained in Tamil Complete Details of GST Kichdy - YouTube. Contextual translation of 'maligai saman list in tamil download' into Tamil. Human translations with examples: tamil, manjal, homelites, maligai saman.
Securing the new way of working from anywhere
Forcepoint CSG is a converged cloud security service that provides visibility, control, and threat protection for users and data, wherever they are. Integrated functionality reduces time to value and ensures maximum capabilities are available. Eliminating multiple point products enables enterprises to cut costs, reduce complexity, and decrease operational overhead while eliminating overlap between product and security teams.
Enterprise security has transformed—people are the new perimeter. In the early 2000s, security efforts still focused on building walls. In the last 10 years, virtualisation gave rise to the public cloud industry and sparked big data. Beyond introducing cloud capabilities to companies, this shift highlighted the importance of protecting critical electronic data. Because users and data are located everywhere today, it’s created a challenging reality for CISOs: We need to secure our users and data anywhere, at any time, on any device.
As the concept of people as the new perimeter becomes the new reality, it’s about protecting users and data in a distributed and diverse environment, one that bridges traditional on-premises infrastructure, including the home office, to multi-cloud and multi-SaaS environments. Our current situation has forced a rapid shift toward supporting large groups of remote workers. It’s a change that’s ushered in a new way of working. And that’s placed even more importance on protecting users and data in hybrid IT environments.
Convergence
- What used to be a product is now often a feature; to us, convergence means merging web security, network security, and cloud application security, delivered in a single, easy-to-consume service.

Security-as-a-Service
- Secure Access Service Edge (SASE) requires organisations to secure the cloud from the cloud. This requires a shift in thinking from infrastructure-centric components to user- and cellpadding='0' border='0'>Product HighlightsDescriptionSuperior user experience
- One SKU to purchase
- One login to access all functionality
- One status page
- One phone number for support
- Anti-virus, anti-malware, cryptocurrency & ransomware› URL and content filtering, and categorisation› SSL inspection
- Threat Ingest API› Advanced Classification Engine (ACE)
- Shared global threat intelligence & ThreatSeeker
- Cloud sandboxing with machine learning
- Inbound and outbound protection
- File blocking
- Acceptable use policies and controls
- Reporting – (drag & drop UI)› Quota enforcement
- Rules-based policy application (adaptive)
- SIEM & AD integration
- Universal policy application
- Customised dashboard view: end user vs. auditor
- ISO 27001, IS27018, CSA STAR, SOC 1 & 2. Certifications at every physical data center covering the entire operations lifecycle
- Real-time updates
- Fault-tolerant, high availability & high performance
- 160+ Points of Presence (PoPs) with coverage across 145 countries
- Content localisation› SLA
- Shadow IT discovery
- Cloud application control
- Inline and reverse proxy, and API mode
- Behavioral analytics
- Anomaly detection
- Incident risk ranking
- PCI, HIPPA
- Fingerprinting
- Drip DLP
- Phishing
Securing the new way of working from anywhere

Forcepoint CSG is a converged cloud security service that provides visibility, control, and threat protection for users and data, wherever they are. Integrated functionality reduces time to value and ensures maximum capabilities are available. Eliminating multiple point products enables enterprises to cut costs, reduce complexity, and decrease operational overhead while eliminating overlap between product and security teams.
Enterprise security has transformed—people are the new perimeter. In the early 2000s, security efforts still focused on building walls. In the last 10 years, virtualisation gave rise to the public cloud industry and sparked big data. Beyond introducing cloud capabilities to companies, this shift highlighted the importance of protecting critical electronic data. Because users and data are located everywhere today, it’s created a challenging reality for CISOs: We need to secure our users and data anywhere, at any time, on any device.
As the concept of people as the new perimeter becomes the new reality, it’s about protecting users and data in a distributed and diverse environment, one that bridges traditional on-premises infrastructure, including the home office, to multi-cloud and multi-SaaS environments. Our current situation has forced a rapid shift toward supporting large groups of remote workers. It’s a change that’s ushered in a new way of working. And that’s placed even more importance on protecting users and data in hybrid IT environments.
Convergence
Maligai Saman List In Tamil Excel Pdf
- What used to be a product is now often a feature; to us, convergence means merging web security, network security, and cloud application security, delivered in a single, easy-to-consume service.
Security-as-a-Service
Tamil Language Maligai Saman List In Tamil Excel Download
- Secure Access Service Edge (SASE) requires organisations to secure the cloud from the cloud. This requires a shift in thinking from infrastructure-centric components to user- and cellpadding='0' border='0'>Product HighlightsDescriptionSuperior user experience
- One SKU to purchase
- One login to access all functionality
- One status page
- One phone number for support
- Anti-virus, anti-malware, cryptocurrency & ransomware› URL and content filtering, and categorisation› SSL inspection
- Threat Ingest API› Advanced Classification Engine (ACE)
- Shared global threat intelligence & ThreatSeeker
- Cloud sandboxing with machine learning
- Inbound and outbound protection
- File blocking
- Acceptable use policies and controls
- Reporting – (drag & drop UI)› Quota enforcement
- Rules-based policy application (adaptive)
- SIEM & AD integration
- Universal policy application
- Customised dashboard view: end user vs. auditor
- ISO 27001, IS27018, CSA STAR, SOC 1 & 2. Certifications at every physical data center covering the entire operations lifecycle
- Real-time updates
- Fault-tolerant, high availability & high performance
- 160+ Points of Presence (PoPs) with coverage across 145 countries
- Content localisation› SLA
- Shadow IT discovery
- Cloud application control
- Inline and reverse proxy, and API mode
- Behavioral analytics
- Anomaly detection
- Incident risk ranking
- PCI, HIPPA
- Fingerprinting
- Drip DLP
- Phishing